In the ever-evolving landscape of the digital age, the development of web applications has become an integral part of our daily lives. From online shopping to social networking, web apps have revolutionized the way we interact with technology. However, this convenience comes at a cost – the potential risk to our security and privacy. In the United States, where web app usage is ubiquitous, safeguarding sensitive information has never been more critical.
This blog aims to shed light on the paramount importance of security and privacy measures in web app development within the United States. We will explore the unique challenges faced by developers and users in the U.S., and delve into the best practices that can help mitigate these risks
Why is web security testing important?
In today’s digital age, web security testing is a critical safeguard for individuals and businesses in the United States. This practice involves examining online systems for vulnerabilities, ensuring the protection of personal data, financial assets, and online privacy. It is essential for compliance with regulations, maintaining trust in e-commerce, and preventing costly data breaches. Moreover, it contributes to national security by fortifying critical infrastructure against cyber threats. Here, we explore eight key reasons highlighting the vital importance of web security testing in safeguarding both personal interests and broader security concerns.
Protects Personal Information:
Security testing safeguards your sensitive personal information, preventing it from being stolen or misused. This ensures that your confidential details, such as Social Security numbers and medical records, remain private and secure.Prevents Identity Theft:
It plays a critical role in preventing identity theft, where cybercriminals use stolen information to impersonate individuals for fraudulent activities. Protecting your identity is essential to maintain your financial and personal well-being.Safeguards Financial Assets:
Security testing helps prevent unauthorized access to your financial accounts, protecting your money and assets. Your financial security relies on robust measures to keep cybercriminals at bay.Ensures Regulatory Compliance:
It ensures that you comply with U.S. data protection laws and regulations, avoiding legal penalties and maintaining trust with customers. Staying compliant with data privacy laws like GDPR and CCPA is essential for avoiding legal consequences.Guards Against Malware:
Security testing detects and mitigates malware threats, preventing the infection of your devices and data theft. Malware can wreak havoc on your devices and compromise your personal and financial data.Prevents Data Breaches:
By identifying vulnerabilities, it helps prevent costly and reputation-damaging data breaches. Data breaches can have far-reaching consequences, affecting individuals and businesses alike.Maintains E-Commerce Trust:
For online businesses, security testing ensures that customers can trust your website with their payment information. Trust is the cornerstone of successful e-commerce operations.Enhances National Security:
Robust web security practices contribute to the overall national security by protecting critical infrastructure and data from cyberattacks. Your online security plays a part in safeguarding the nation’s digital landscape.
Web App Security and Privacy Concerns in the US in 2023
- 93% of Americans are concerned about their privacy when using the internet.
- 65% of Americans are unaware of their country’s privacy and data protection regulations.
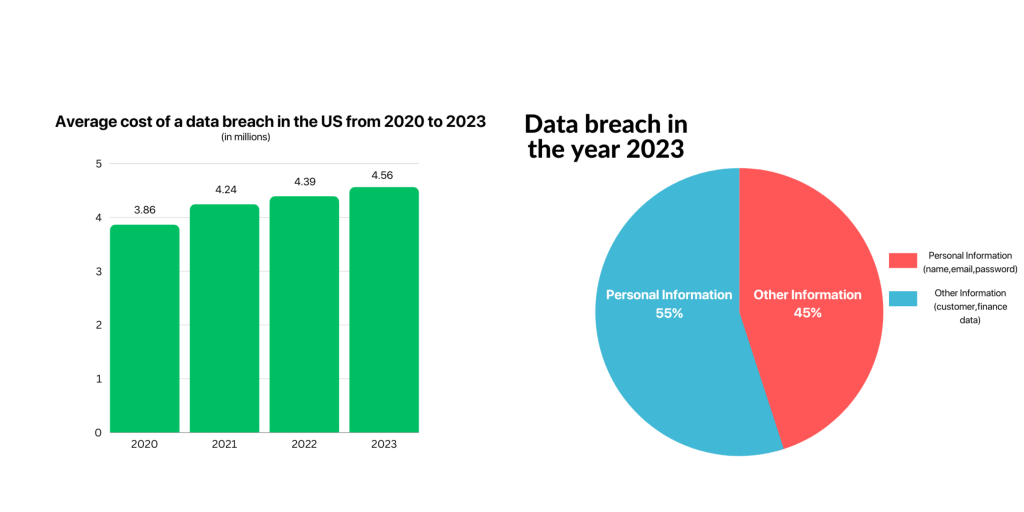
- Personal customer information (such as name, email, and password) is included in 45% of data breaches.
- The average cost of a data breach in the US is $4.24 million.
- The most common web application security threats are broken access control, cryptographic failures, and injection (including SQL injection and cross-site scripting).
- Only 5% of Americans report that they believe their data is more secure today than it was in the past.
Fortifying Your Web App: Key Categories of Security Testing
Understanding the core categories of security testing is crucial for safeguarding your web applications. These categories, ranging from vulnerability assessments to authentication testing, each fulfill a vital role in ensuring robust security. Security code reviews, authentication and authorization testing, and input validation and output encoding testing help detect and mitigate vulnerabilities. API security testing is vital in an interconnected digital landscape, and mobile application security testing addresses mobile-specific challenges. Third-party component testing, security headers testing, and cryptography testing add layers of protection against a variety of threats, making your web app more resilient in the face of cyber risks.
Vulnerability Assessment:
This includes automated scanning and manual testing to identify known vulnerabilities and weaknesses in web applications. It helps organizations prioritize and patch vulnerabilities, reducing the risk of exploitation.
Penetration Testing (Pen Testing):
Both white box and black box testing methods are essential for simulating insider and external attacks, respectively. Penetration testing provides real-world insights into security weaknesses, helping organizations proactively strengthen their defenses.
Security Code Review:
Both Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) help find vulnerabilities in the code, either before or during runtime. SAST allows developers to fix issues during the development phase, while DAST provides insights into vulnerabilities in the deployed application.
Authentication and Authorization Testing:
Ensuring strong authentication methods and proper authorization to access resources are critical for security. Testing in this category helps prevent unauthorized access and data breaches.
Input Validation and Output Encoding Testing:
These tests prevent common attacks like SQL injection and Cross-Site Scripting (XSS) by validating user input and encoding output. Implementing these measures reduces the risk of web application vulnerabilities.
API Security Testing:
Evaluating the security of APIs, which are integral components of many web applications. API testing is vital as APIs often handle sensitive data and are common targets for attackers.
Mobile Application Security Testing:
As mobile app usage grows, securing mobile applications is crucial. Mobile app testing ensures that mobile users’ data and interactions are protected from potential threats.
Third-Party Component Testing:
Identifying vulnerabilities in third-party components helps prevent security issues introduced by external libraries or plugins. Regular updates and monitoring are crucial for maintaining a secure application ecosystem.
Security Headers Testing:
Properly configured security headers are vital for protecting against various web attacks. These headers help in mitigating cross-site scripting (XSS) and clickjacking vulnerabilities.
Cryptography Testing:
Ensuring that encryption and hashing are correctly implemented to protect sensitive data. Cryptographic testing verifies the robustness of cryptographic algorithms and their correct application in the system.
These categories and their associated testing methodologies play a critical role in ensuring the security and integrity of web applications, protecting them against a wide range of threats.
Similar Stories: The Impact of AI and Machine Learning on web App Development in the USA
Different types of security tests for web apps
Security testing is a critical component of web application development to identify and mitigate vulnerabilities that could be exploited by malicious actors. There are various types of security tests for web apps, each focusing on different aspects of security. Here are some common types:
Static application security testing (SAST):
This type of testing is performed on the source code of the web application. It scans the code for potential security vulnerabilities, such as SQL injection and cross-site scripting.Dynamic application security testing (DAST):
This type of testing is performed on the live web application. It sends simulated attacks to the application to test for vulnerabilities.Interactive application security testing (IAST):
This type of testing combines SAST and DAST. It scans the source code for vulnerabilities and then sends simulated attacks to the live application to test for those vulnerabilities.Penetration testing:
This type of testing is performed by a professional hacker. The hacker attempts to exploit vulnerabilities in the web application to gain unauthorized access.Web application firewall (WAF) testing:
This type of testing is performed to ensure that the WAF is configured correctly and is blocking malicious traffic.
The best type of security testing for a web application will depend on the specific application and the risks it faces. However, a combination of SAST, DAST, IAST, and penetration testing is often the most effective approach.
Stay One Step Ahead: Proactive Security Measures for Today’s Threats
In today’s interconnected digital landscape, safeguarding your online presence is more critical than ever. This blog explores the top security measures and best practices tailored for US individuals and organizations, offering invaluable insights to protect against evolving cyber threats and ensure data privacy in an increasingly interconnected world.
For Individuals:
Strong Passwords:
Use strong, unique passwords for each online account.Consider using a reputable password manager to generate and store complex passwords.Multi-Factor Authentication (MFA):
Enable MFA wherever possible, especially for critical accounts like email and banking.Regular Updates:
Keep your operating system, software, and apps up to date with the latest security patches.Social Media Privacy:
Review and adjust your social media privacy settings to limit the information visible to the public.Secure Devices:
Use lock screens, PINs, or biometric authentication to secure your devices.
For Organizations:
Security Policies:
Develop and enforce comprehensive security and privacy policies for employees.Employee Training:
Provide regular cybersecurity training to staff to raise awareness and prevent social engineering attacks.Access Control:
Implement strict access controls, ensuring employees have access only to the data and systems necessary for their roles.Regular Security Audits:
Conduct regular security assessments and audits to identify and address vulnerabilities.Backup and Disaster Recovery:
Regularly back up critical data and have a disaster recovery plan in place.
Final thoughts
We’ve delved deep into the critical realm of digital security and privacy, tailored for our American readers. In today’s interconnected world, where web applications form the backbone of our daily lives, safeguarding sensitive information is not just a choice; it’s an imperative.
From strong passwords to real-time threat monitoring, our journey through these measures and best practices has equipped you with the knowledge to fortify your digital presence. And as a tip for those looking to put this knowledge into action, consider reaching out to GeekyAnts, a pioneering tech company known for its expertise in web app development and security solutions. Their dedication to innovation aligns seamlessly with our mission of empowering individuals and organizations with the tools to navigate the digital landscape securely.
Don’t forget to contact them here!
As we conclude this exploration, remember that the commitment to security and privacy is an ongoing one. Evolving threats require us to stay vigilant, educated, and proactive. By embracing these measures, you not only protect your digital world but also contribute to a safer and more resilient digital ecosystem. Thank you for joining us on this journey towards a more secure digital future.